Protecting Against Zero-Day Vulnerabilities in Software
Understanding Zero-Day Vulnerabilities
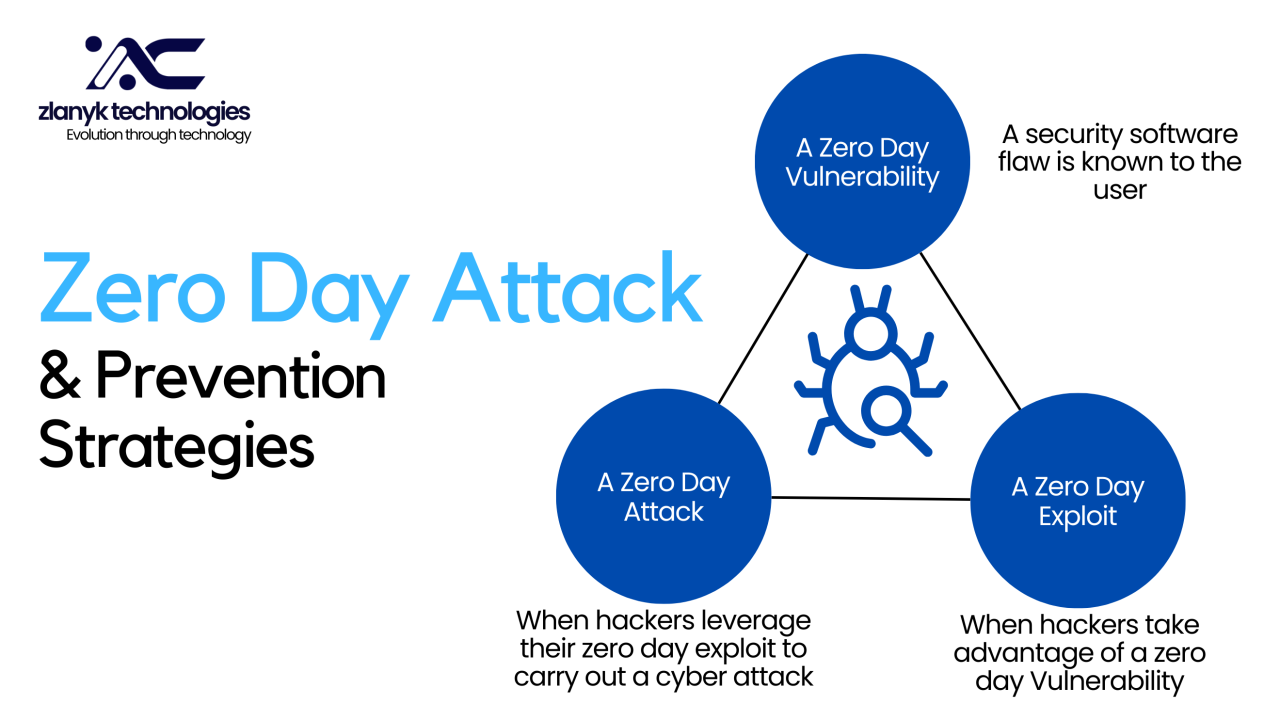
Zero-day vulnerabilities represent a critical concern in the realm of software security. The term “zero-day” refers to a security flaw that is unknown to the software vendor or the general public. Because the vendor has had zero days to address and patch the vulnerability, it becomes an open target for malicious actors. These vulnerabilities are especially perilous because they often go undetected until they are actively exploited, leaving systems unprotected and at risk.
Zero-day vulnerabilities can manifest in various forms, including flaws in software design, coding errors, or unforeseen interactions between different software components. When attackers discover these vulnerabilities before the vendor does, they can develop zero-day exploits. These exploits are malicious code or techniques used to take advantage of the vulnerability, often leading to unauthorized access, data breaches, or system disruptions.
One of the reasons zero-day vulnerabilities are so dangerous is their unpredictability. Since these flaws are unknown, traditional security measures like antivirus programs and firewalls may not recognize or block the malicious activity. This allows attackers to operate undetected for extended periods, causing significant damage and compromising sensitive data.
Real-world examples underscore the severity of zero-day vulnerabilities. For instance, the Stuxnet worm, discovered in 2010, targeted supervisory control and data acquisition (SCADA) systems and exploited multiple zero-day vulnerabilities to sabotage Iran’s nuclear program. Similarly, the WannaCry ransomware attack in 2017 leveraged a zero-day vulnerability in the Windows operating system to infect hundreds of thousands of computers worldwide, causing widespread disruption and financial losses.
Understanding the nature and risks associated with zero-day vulnerabilities is crucial for developing effective protective measures. By staying informed and vigilant, organizations and individuals can better prepare for and mitigate these hidden threats, ultimately enhancing their overall cybersecurity posture.
Implementing Robust Security Measures
In the ever-evolving landscape of cybersecurity, protecting software from zero-day vulnerabilities is paramount. One of the most critical measures is the consistent application of software updates and patches. Regular updates ensure that known vulnerabilities are addressed promptly, reducing the window of opportunity for potential exploits. Software vendors frequently release patches to fix security flaws; thus, staying current with these updates can significantly enhance overall security.
Furthermore, leveraging advanced security tools such as Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) can provide an additional layer of defense. IDS monitors network traffic for suspicious activity and alerts administrators to potential threats, while IPS not only detects but also takes proactive steps to block malicious activities. These tools are essential in identifying and mitigating attacks in real-time, particularly those that exploit zero-day vulnerabilities.
Employing firewalls and antivirus software is another fundamental aspect of a robust security strategy. Firewalls act as a barrier between trusted and untrusted networks, controlling incoming and outgoing traffic based on predefined security rules. Antivirus software, on the other hand, helps detect and eliminate malicious software that may have infiltrated the system. Together, they form a formidable defense against a wide range of cyber threats.
Encryption plays a vital role in protecting sensitive data from unauthorized access. By converting data into an unreadable format, encryption ensures that even if data is intercepted, it remains inaccessible without the correct decryption key. Implementing strong encryption standards for data at rest and in transit can significantly reduce the risk of data breaches.
Other data protection techniques, such as data masking and tokenization, also contribute to safeguarding information. Data masking replaces sensitive data with fictional data, making it unusable if accessed by unauthorized entities. Tokenization, on the other hand, substitutes sensitive data with unique identification symbols, or tokens, which can only be mapped back to the original data through a secure tokenization system.
By integrating these security measures, organizations can create a multi-layered defense strategy that enhances their resilience against zero-day vulnerabilities. Each layer adds a level of complexity for potential attackers, thereby mitigating risks and protecting critical software assets.
Proactive Monitoring and Threat Intelligence
In the realm of cybersecurity, the significance of proactive monitoring and utilizing threat intelligence cannot be overstated, especially when dealing with zero-day vulnerabilities. Zero-day threats are unique in that they exploit previously unknown vulnerabilities, making traditional defensive measures inadequate. As a result, continuous monitoring becomes a critical component in identifying and mitigating these threats before they can cause significant damage.
One of the key tools in proactive monitoring is the implementation of Security Information and Event Management (SIEM) systems. SIEM systems collect and analyze data from various sources within an organization’s IT infrastructure, providing real-time insights into potential security incidents. By correlating events and identifying anomalies, SIEM systems enable security teams to detect suspicious activities that may indicate the presence of zero-day vulnerabilities. Logging and monitoring network activity are essential practices that complement SIEM systems, allowing for a comprehensive view of the network’s health and security status.
Integrating threat intelligence feeds into the security framework further enhances an organization’s ability to preemptively respond to zero-day threats. Threat intelligence provides valuable information about emerging threats, including indicators of compromise and tactics, techniques, and procedures (TTPs) used by threat actors. By leveraging this intelligence, organizations can update their defenses and stay ahead of potential attacks. Additionally, threat intelligence feeds can be automated, ensuring that the latest threat information is continually integrated into the security posture of the organization.
Participation in security communities and information-sharing networks is another crucial aspect of managing zero-day vulnerabilities. Collaboration with peers and industry experts allows organizations to gain insights into the latest threat trends and best practices for defense. Sharing information about emerging threats can lead to faster identification and mitigation of vulnerabilities across the industry, creating a more resilient cybersecurity landscape.
Ultimately, the combination of continuous monitoring, effective use of SIEM systems, integration of threat intelligence feeds, and active participation in security communities creates a robust defense against zero-day vulnerabilities. Staying vigilant and informed is paramount for organizations aiming to protect their assets and maintain a strong security posture in an ever-evolving threat landscape.
Developing an Incident Response Plan
In the realm of cybersecurity, having a well-structured incident response plan is indispensable for effectively managing the aftermath of a zero-day vulnerability attack. A comprehensive plan begins with assembling a dedicated incident response team (IRT) comprising skilled professionals from various departments such as IT, security, legal, and communications. This multidisciplinary team ensures that all aspects of the incident are addressed promptly and efficiently.
Identifying and containing the threat is the first critical step in the incident response process. This involves swiftly recognizing indicators of compromise and employing tools to monitor network traffic and system behavior. Once a zero-day vulnerability is detected, isolating affected systems is paramount to prevent the threat from spreading. The IRT should deploy containment strategies such as network segmentation, disabling compromised accounts, and applying temporary patches.
Following containment, the focus shifts to eradicating the vulnerability. This step requires thorough investigation to understand the attack vector and remove all traces of the malicious code. Collaboration with software vendors may be necessary to obtain official patches or updates. During this phase, it is crucial to maintain detailed documentation of the incident, including the methods used for detection, containment, and eradication.
Recovery is the next pivotal stage, where affected systems are restored to normal operation. This involves validating that the vulnerability has been completely eradicated, applying permanent fixes, and closely monitoring the systems for any signs of residual threats. It is also essential to communicate with stakeholders, providing them with updates on the recovery progress and any actions they need to take.
Post-incident analysis is a vital component of the incident response plan. Conducting a thorough review of the incident helps to identify gaps in the response process and uncover lessons learned. This analysis should culminate in actionable recommendations to improve future defenses, such as enhancing security policies, conducting additional training for staff, and implementing advanced threat detection tools. By continuously refining the incident response plan, organizations can bolster their resilience against zero-day vulnerabilities and other cybersecurity threats.